Category: windows
TightVNC Security Hole
Virtual Network Computing (VNC) is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It transmits the keyboard and mouse input from one computer to another, relaying the graphical-screen updates, over a network.[1]
VNC servers work on a variety of platforms, allowing you to share screens and keyboards between Windows, Mac, Linux, and Raspberry Pi devices. RDP server is proprietary and only works with one operating system. VNC vs RDP performance. RDP provides a better and faster remote connection.
There are a number of reasons why people use it.
There are a few VNC tools out there.
RealVNC
UltraVNC – Best one to use.
Tight-VNC – Security Hole
Tight-VNC has their encryption algorithm hardcoded into its software and appears they have NOT updated its encryption standards in years.
DES Encryption used
# This is hardcoded in VNC applications like TightVNC.
$magicKey = [byte[]]@(0xE8, 0x4A, 0xD6, 0x60, 0xC4, 0x72, 0x1A, 0xE0)
$ansi = [System.Text.Encoding]::GetEncoding(
[System.Globalization.CultureInfo]::CurrentCulture.TextInfo.ANSICodePage)
$pass = [System.Net.NetworkCredential]::new(”, $Password).Password
$byteCount = $ansi.GetByteCount($pass)
if ($byteCount –gt 8) {
$err = [System.Management.Automation.ErrorRecord]::new(
[ArgumentException]‘Password must not exceed 8 characters’,
‘PasswordTooLong‘,
[System.Management.Automation.ErrorCategory]::InvalidArgument,
$null)
$PSCmdlet.WriteError($err)
return
}
$toEncrypt = [byte[]]::new(8)
$null = $ansi.GetBytes($pass, 0, $pass.Length, $toEncrypt, 0)
$des = $encryptor = $null
try {
$des = [System.Security.Cryptography.DES]::Create()
$des.Padding = ‘None’
$encryptor = $des.CreateEncryptor($magicKey, [byte[]]::new(8))
$data = [byte[]]::new(8)
$null = $encryptor.TransformBlock($toEncrypt, 0, $toEncrypt.Length, $data, 0)
, $data
}
finally {
if ($encryptor) { $encryptor.Dispose() }
if ($des) { $des.Dispose() }
}
}
What this means is…IF you are using admin credentials on your machine while using Tight-VNC a hacker that is way better than I… Could gain access to your infrastructure by simply glimpsing the windows registry. Im sure there ways to exploit it.
I will demonstrate:
Now you can install Tight-vnc manually or via chocolatey. I used chocolatey and this from a public available repo.
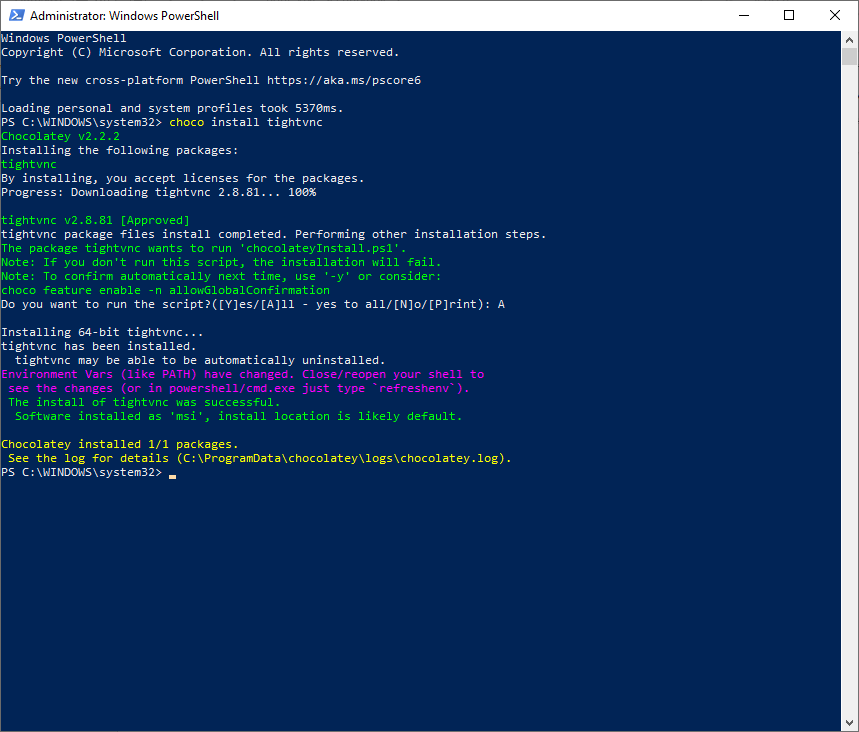
Now lets set the password by right clicking tightvnc icon in the bottom corner and setting the password to an 8 character password, by clicking on change primary password and typing in whatever you like
‘Suck3r00’
Now lets open powershell without administrator privileges. Lets say I got in remotely and chocolatey is there and I want to check to see if tight-vnc is there.
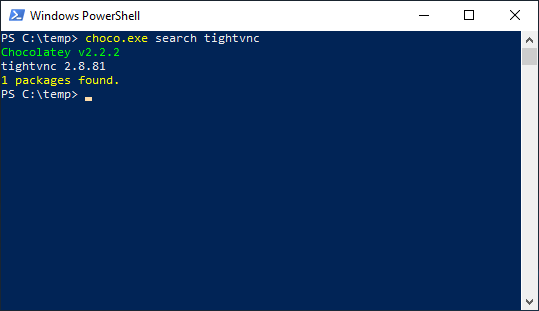
As you can see I find this without administrator privilege.
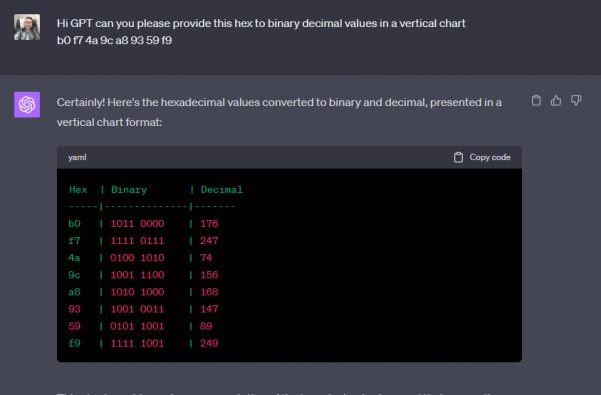
Now lets say I was able to view the registry and get the encrypted value for tight-vnc; all I need to do is see for a few seconds.
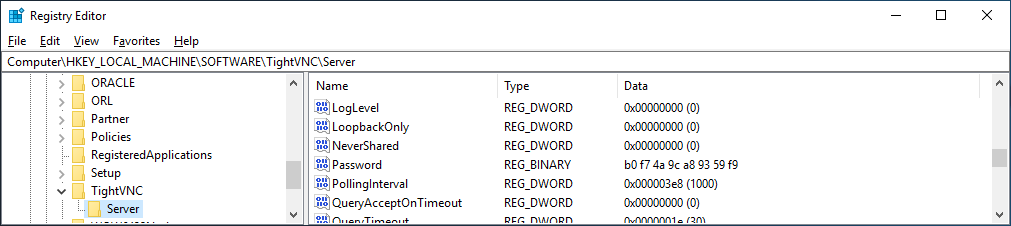
Now there are tools online where you can convert that hexadecimal to binary decimal values long before AI was around. But since I love GPT im going to ask it to convert that for me
I have script that didn’t take long to put together from digging around for about an hour online. Which im obviously not going to share, BUT if I can do it……someone with skills could do pretty easy. A professional hacker NO SWEAT.
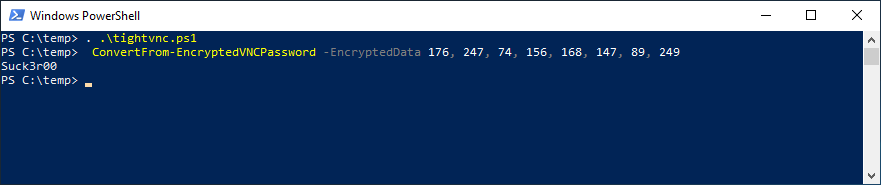
As you can see if you have rolled this out how dangerous it is.
Having said that I have also written an Ansible Role which will purge tightvnc from your infrastructure and deploy ultravnc which will use encryption and AD authentication. Which the other two currently do NOT do.
Hope you enjoyed getting P0WNed.
How to Deploy VM’s in Hyper-V with Ansible
Thought it would be fun to do…..
If you can find another public repo that has it working online. Please send me a message so I can kick myself.
How to use this role: ansible-hyperv repo is set to private you must request access
Example file: hosts.dev, hosts.staging, hosts.prod
Note: If there is no group simply list the server outside grouping, the –limit flag will pick it
up.
Descriptions:
Operational Use:
Descriptions:
Operational Use:
passed parameters: example: inventory/host_vars/testmachine.nicktailor.com
vms:
– type: testserver
name: “nicktest“
cpu: 2
memory: 4096MB
network:
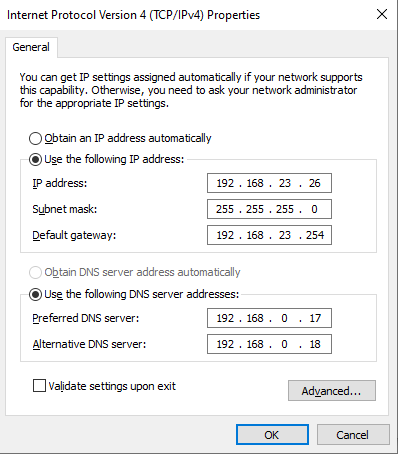
ip: 192.168.23.26
netmask: 255.255.255.0
gateway: 192.168.23.254
dns: 192.168.0.17,192.168.0.18
# network_switch: ‘External Virtual Switch’
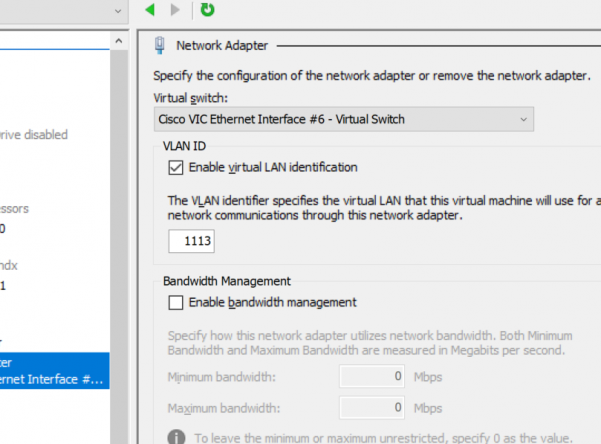
network_switch: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’
vlanid: 1113
# source-image
src_vhd: ‘Z:\volumes\devops\devopssysprep\devopssysprep.vhdx‘
# destination will be created in Z:\\volumes\servername\servername.vhdx by default
# to change the paths you need to update the prov_vm.yml’s first three task paths
Running your playbook:
Example: of ansible/createvm.yml
—
– name: Provision VM
hosts: hypervdev.nicktailor.com
gather_facts: no
tasks:
– import_tasks: roles/ansible-hyperv/tasks/prov_vm.yml
Command:
ansible-playbook –i inventory/dev/hosts createvm.yml ––limit=’testmachine1.nicktailor.com‘
Successful example run of the book:
[ntailor@ansible-home ~]$ ansible-playbook –i inventory/hosts createvm.yml –limit=’testmachine1.nicktailor.com‘
PLAY [Provision VM] ****************************************************************************************************************************************************************
TASK [Create directory structure] **************************************************************************************************************************************************
ok: [testmachine1.nicktailor.com] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [Check whether vhdx already exists] *******************************************************************************************************************************************
ok: [testmachine1.nicktailor.com] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [Clone vhdx] ******************************************************************************************************************************************************************
changed: [testmachine1.nicktailor.com] => (item={‘changed’: False, ‘invocation’: {‘module_args‘: {‘path’: ‘Z:\\\\volumes\\\\devops\\nicktest\\nicktest.vhdx‘, ‘checksum_algorithm‘: ‘sha1’, ‘get_checksum‘: False, ‘follow’: False, ‘get_md5’: False}}, ‘stat’: {‘exists’: False}, ‘failed’: False, ‘item’: {‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘}, ‘ansible_loop_var‘: ‘item’})
TASK [set_fact] ********************************************************************************************************************************************************************
ok: [testmachine1.nicktailor.com]
TASK [debug] ***********************************************************************************************************************************************************************
ok: [testmachine1.nicktailor.com] => {
“path_folder“: “Z:\\\\volumes\\\\devops\\nicktest\\nicktest.vhdx”
}
TASK [set_fact] ********************************************************************************************************************************************************************
ok: [testmachine1.nicktailor.com]
TASK [debug] ***********************************************************************************************************************************************************************
ok: [testmachine1.nicktailor.com] => {
“page_folder“: “Z:\\\\volumes\\\\devops\\nicktest”
}
TASK [Create VMs] ******************************************************************************************************************************************************************
changed: [testmachine1.nicktailor.com] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [Set SmartPaging File Location for new Virtual Machine to use destination image path] *****************************************************************************************
changed: [testmachine1.nicktailor.com] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [Set Network VlanID] **********************************************************************************************************************************************************
changed: [testmachine1.nicktailor.com] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [Configure VMs IP] ************************************************************************************************************************************************************
changed: [testmachine1.nicktailor.com] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [add_host] ********************************************************************************************************************************************************************
changed: [testmachine1.nicktailor.com] => (item={‘changed’: True, ‘failed’: False, ‘item’: {‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘}, ‘ansible_loop_var‘: ‘item’})
TASK [Poweron VMs] *****************************************************************************************************************************************************************
changed: [testmachine1.nicktailor.com] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [Wait for VM to be running] ***************************************************************************************************************************************************
ok: [testmachine1.nicktailor.com -> localhost] => (item={‘type’: ‘testservers‘, ‘name’: ‘nicktest‘, ‘cpu‘: 2, ‘memory’: ‘4096MB’, ‘network’: {‘ip‘: ‘192.168.23.36’, ‘netmask’: ‘255.255.255.0’, ‘gateway’: ‘192.168.23.254’, ‘dns‘: ‘192.168.0.17,192.168.0.18‘}, ‘network_switch‘: ‘Cisco VIC Ethernet Interface #6 – Virtual Switch’, ‘vlanid‘: 1113, ‘src_vhd‘: ‘C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx‘})
TASK [debug] ***********************************************************************************************************************************************************************
ok: [testmachine1.nicktailor.com] => {
“wait”: {
“changed”: false,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: false,
“elapsed”: 82,
“failed”: false,
“invocation”: {
“module_args“: {
“active_connection_states“: [
“ESTABLISHED”,
“FIN_WAIT1”,
“FIN_WAIT2”,
“SYN_RECV”,
“SYN_SENT”,
“TIME_WAIT”
],
“connect_timeout“: 5,
“delay”: 0,
“exclude_hosts“: null,
“host”: “192.168.23.36”,
“msg“: null,
“path”: null,
“port”: 5986,
“search_regex“: null,
“sleep”: 1,
“state”: “started”,
“timeout”: 100
}
},
“item”: {
“cpu“: 2,
“memory”: “4096MB”,
“name”: “nicktest“,
“network”: {
“dns“: “192.168.0.17,192.168.0.18“,
“gateway”: “192.168.23.254”,
“ip“: “192.168.23.36”,
“netmask”: “255.255.255.0”
},
“network_switch“: “Cisco VIC Ethernet Interface #6 – Virtual Switch”,
“src_vhd“: “C:\\volumes\\devops\\devopssysprep\\devopssysprep.vhdx”,
“type”: “testservers“,
“vlanid“: 1113
},
“match_groupdict“: {},
“match_groups“: [],
“path”: null,
“port”: 5986,
“search_regex“: null,
“state”: “started”
}
]
}
}
PLAY RECAP *************************************************************************************************************************************************************************
testmachine1.nicktailor.com : ok=15 changed=7 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
How to Join Windows Servers to your DC with Ansible
How to use this role:
Example file: hosts.dev, hosts.staging, hosts.prod
Note: If there is no group simply list the server outside grouping, the –limit flag will pick it
up.
Descriptions:
Operational Use:
Descriptions:
Operational Use:
passed parameters: example: roles/add-server-to-dc/default/main.yml
dns_domain_name: ad.nicktailor.com
computer_name: testmachine1
domain_ou_path: “OU=Admin,DC=nicktailor,DC=local”
domain_admin_user: adminuser@nicktailor.com
state: domain
Running your playbook:
Example: of ansible/joinservertodomain.yml
– hosts: all
gather_facts: no
vars_prompt:
– name: domain_pass
prompt: Enter Admin Domain Password
roles:
– role: add–servers-to–dc
Command:
ansible-playbook –i inventory/dev/hosts joinservertodomain.yml ––limit=’testmachine1.nicktailor.com‘
Successful example run of the book:
[alfred@ansible.nicktailor.com ~]$ ansible-playbook –i inventory/hosts joinservertodomain.yml –limit=’testmachine1.nicktailor.com‘
ansible-playbook 2.9.27
config file = /etc/ansible/ansible.cfg
configured module search path = [‘/home/alfred/.ansible/plugins/modules’, ‘/usr/share/ansible/plugins/modules’]
ansible python module location = /usr/lib/python3.6/site-packages/ansible
executable location = /usr/bin/ansible-playbook
python version = 3.6.8 (default, Nov 10 2021, 06:50:23) [GCC 8.5.0 20210514 (Red Hat 8.5.0-3.0.2)]
PLAYBOOK: joinservertodomain.yml *****************************************************************************************************************************************************
Positional arguments: joinservertodomain.yml
verbosity: 4
connection: smart
timeout: 10
become_method: sudo
tags: (‘all’,)
inventory: (‘/home/alfred/inventory/hosts’,)
subset: testmachine1.nicktailor.com
forks: 5
1 plays in joinservertodomain.yml
Enter Domain Password:
PLAY [all] ***********************************************************************************************************************************************************************
META: ran handlers
TASK [addservertodc : Join windows host to Domain Controller] ********************************************************************************************************************
task path: /home/alfred/roles/addservertodc/tasks/main.yml:1
Using module file /usr/lib/python3.6/site-packages/ansible/modules/windows/win_domain_membership.ps1
Pipelining is enabled.
<testmachine1.nicktailor.com> ESTABLISH WINRM CONNECTION FOR USER: ansibleuser on PORT 5986 TO testmachine1.nicktailor.com
EXEC (via pipeline wrapper)
changed: [testmachine1.nicktailor.com] => {
“changed”: true,
“reboot_required“: true
}
TASK [addservertodc : win_reboot] ************************************************************************************************************************************************
win_reboot: system successfully rebooted
changed: [testmachine1.nicktailor.com] => {
“changed”: true,
“elapsed”: 23,
“rebooted”: true
}
META: ran handlers
META: ran handlers
PLAY RECAP ***********************************************************************************************************************************************************************
testmachine1.nicktailor.com : ok=2 changed=2 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
How to deploy windows firewall rules with Ansible
How to use this role:
Example file: hosts.dev, hosts.staging, hosts.prod
Note: If there is no group simply list the server outside grouping, the –limit flag will pick it
up.
Note: If you do not create a group_var/groupfile or host_var/server file. Then the default/main.yml rules are implemented by this role, you can update this file to have whichever defaults you like and they can be overridden at the group_var and host_var level, should you need to.
Descriptions:
Operational Use:
Descriptions:
Operational Use:
Okay now here is where VSC is handy. You want to connect your visual studio code to the management server under your user. I have provided a link which shows you how to setup your keys and get VSC working with it.
Note: You don’t have to use VSC you can use good old nano or vim, but it’s a pain. Up to you.
defaults/main.yml – this file is the default rules it will apply if you do not add any other rules currently
—
# defaults file for windows_firewall
win_fw_prefix: “Ansible-Created-Rule”
win_fw_ports_allow_in:
– localport: 53,
profile: public
– localport: 123,
profile: public
win_fw_web_ports:
– localport: 80,
profile: public
– localport: 443,
profile: public
– localport: 8080,
profile: public
win_fw_program_allowed_web_out_public:
– ‘microsoftupdate.exe’
Running your playbook:
Example: of ansible/ nickfirewall.yml
– hosts: all
gather_facts: yes
any_errors_fatal: true
roles:
– role: ansible-windows-firewall
Command:
ansible-playbook –i inventory/dev/hosts nickfirewall.yml ––limit=’devops.nicktailor.win‘
Successful example run of the book:
[aflred@batcave.ansible]$ ansible-playbook –i hosts/dev nickfirewall.yml –limit=’devops.nicktailor.win‘
PLAY [all] ***************************************************************************************************************************************************************************
TASK [Gathering Facts] ***************************************************************************************************************************************************************
ok: [devops.nicktailor.win]
TASK [windows_firewall : Enable firewall for Domain, Public and Private profiles] ****************************************************************************************************
ok: [devops.nicktailor.win]
TASK [windows_firewall : Firewall | WebServer System Any Profile] ********************************************************************************************************************
ok: [devops.nicktailor.win] => (item={‘description’: ‘IGMP messages are sent and received by nodes to create, join and depart multicast groups.’, ‘direction’: ‘in’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ‘Any’, ‘name’: ‘CoreNet-IGMP-In’, ‘protocol’: ‘2’, ‘remoteip‘: ‘Any’})
ok: [devops.nicktailor.win] => (item={‘description’: ‘IGMP messages are sent and received by nodes to create, join and depart multicast groups.’, ‘direction’: ‘out’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ‘Any’, ‘name’: ‘CoreNet-IGMP-Out’, ‘protocol’: ‘2’, ‘remoteip‘: ‘Any’})
ok: [devops.nicktailor.win] => (item={‘description’: ‘Inbound rule required to permit IPv6 traffic for ISATAP (Intra-Site Automatic Tunnel Addressing Protocol) and 6to4 tunneling services.’, ‘direction’: ‘in’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ‘Any’, ‘name’: ‘CoreNet-IPv6-In’, ‘protocol’: ’41’, ‘remoteip‘: ‘Any’})
ok: [devops.nicktailor.win] => (item={‘description’: ‘Outbound rule required to permit IPv6 traffic for ISATAP (Intra-Site Automatic Tunnel Addressing Protocol) and 6to4 tunneling services.’, ‘direction’: ‘out’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ‘Any’, ‘name’: ‘CoreNet-IPv6-Out’, ‘protocol’: ’41’, ‘remoteip‘: ‘Any’})
ok: [devops.nicktailor.win] => (item={‘description’: ‘An inbound rule to allow HTTPS traffic for Internet Information Services (IIS) [TCP 443]’, ‘direction’: ‘in’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ‘443’, ‘name’: ‘IIS-WebServerRole-HTTPS-In-TCP’, ‘protocol’: ‘TCP’, ‘remoteip‘: ‘Any’})
ok: [devops.nicktailor.win] => (item={‘description’: ‘Inbound rule to allow SMB traffic to manage the File Services role.’, ‘direction’: ‘in’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ‘445’, ‘name’: ‘FileServer–ServerManager-SMB-TCP-In’, ‘protocol’: ‘TCP’, ‘remoteip‘: ‘Any’})
ok: [devops.nicktailor.win] => (item={‘description’: ‘An inbound rule to allow HTTP traffic for Internet Information Services (IIS) [TCP 80]’, ‘direction’: ‘in’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ’80’, ‘name’: ‘IIS-WebServerRole-HTTP-In-TCP’, ‘protocol’: ‘TCP’, ‘remoteip‘: ‘Any’})
ok: [devops.nicktailor.win] => (item={‘description’: ‘Inbound TCP rule to allow IPHTTPS tunneling technology to provide connectivity across HTTP proxies and firewalls.’, ‘direction’: ‘in’, ‘icmp_type_code‘: ‘Any’, ‘localport‘: ‘IPHTTPSIn‘, ‘name’: ‘CoreNet-IPHTTPS-In’, ‘protocol’: ‘TCP’, ‘remoteip‘: ‘Any’})
TASK [windows_firewall : Firewall | allow incoming ports] ****************************************************************************************************************************
ok: [devops.nicktailor.win] => (item={‘localport‘: 53, ‘profile’: ‘public’})
ok: [devops.nicktailor.win] => (item={‘localport‘: 123, ‘profile’: ‘public’})
ok: [devops.nicktailor.win] => (item={‘localport‘: 80, ‘profile’: ‘public’})
ok: [devops.nicktailor.win] => (item={‘localport‘: 443, ‘profile’: ‘public’})
ok: [devops.nicktailor.win] => (item={‘localport‘: 8080, ‘profile’: ‘public’})
TASK [windows_firewall : Firewall | allow outgoing program] **************************************************************************************************************************
ok: [devops.nicktailor.win] => (item=microsoftupdate.exe)
PLAY RECAP ***************************************************************************************************************************************************************************
devops.nicktailor.win : ok=5 changed=0 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
How to deploy windows shares with Ansible
How to use this role:
Example file: hosts.dev, hosts.staging, hosts.prod
Note: If there is no group simply list the server outside grouping, the –limit flag will pick it
up.
Descriptions:
Operational Use:
Descriptions:
Operational Use:
Okay now here is where VSC is handy. You want to connect your visual studio code to the management server under your user. I have provided a link which shows you how to setup your keys and get VSC working with it.
Note: You don’t have to use VSC you can use good old nano or vim, but it’s a pain. Up to you.
Running your playbook:
Example: of ansible/ nickcreateshare.yml
– hosts: all
gather_facts: yes
any_errors_fatal: true
roles:
– role: ansible-windows-share
Command:
ansible-playbook –i inventory/dev/hosts nickcreateshare.yml ––limit=’devops.nicktailor.win‘
Successful example run of the book:
[BruceWayne@batcave.ansible ~]$ ansible-playbook –i inventory/hosts nickcreateshare.yml –limit=‘devops.nicktailor.win
PLAY [all] ***************************************************************************************************************************************************************************
TASK [Gathering Facts] ***************************************************************************************************************************************************************
ok: [‘devops.nicktailor.win]
TASK [create-windows-share : Create share path] **************************************************************************************************************************************
changed: [‘devops.nicktailor.win] => (item={‘share_name‘: ‘test3’, ‘description_share‘: ‘default share for testing’, ‘share_path‘: ‘C:\\inetpub\\wwwroot3′, ‘change’: ‘ansibleuser‘, ‘list’: True, ‘allowed_users‘: ‘ansibleuser‘, ‘user_permissions‘: ‘ansibleuser‘})
TASK [create-windows-share : debug] **************************************************************************************************************************************************
ok: [‘devops.nicktailor.win] => {
“path”: {
“changed”: true,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: true,
“failed”: false,
“item”: {
“allowed_users“: “ansibleuser“,
“change”: “ansibleuser“,
“description_share“: “default share for testing”,
“list”: true,
“share_name“: “test3”,
“share_path“: “C:\\inetpub\\wwwroot3″,
“user_permissions“: “ansibleuser“
}
}
]
}
}
TASK [create-windows-share : Add public company share] *******************************************************************************************************************************
changed: [‘devops.nicktailor.win] => (item={‘share_name‘: ‘test3’, ‘description_share‘: ‘default share for testing’, ‘share_path‘: ‘C:\\inetpub\\wwwroot3′, ‘change’: ‘ansibleuser‘, ‘list’: True, ‘allowed_users‘: ‘ansibleuser‘, ‘user_permissions‘: ‘ansibleuser‘})
TASK [create-windows-share : debug] **************************************************************************************************************************************************
ok: [‘devops.nicktailor.win] => {
“share”: {
“changed”: true,
“msg“: “All items completed”,
“results”: [
{
“actions”: [
“New-SmbShare -Name test3 -Path C:\\inetpub\\wwwroot3″,
“Set-SmbShare -Force -Name test3 -Description default share for testing”,
“Revoke-SmbShareAccess -Force -Name test3 –AccountName Everyone”,
“Grant-SmbShareAccess -Force -Name test3 –AccountName DEVOPS01\\ansibleuser –AccessRight Full”
],
“ansible_loop_var“: “item”,
“changed”: true,
“failed”: false,
“item”: {
“allowed_users“: “ansibleuser“,
“change”: “ansibleuser“,
“description_share“: “default share for testing”,
“list”: true,
“share_name“: “test3”,
“share_path“: “C:\\inetpub\\wwwroot3″,
“user_permissions“: “ansibleuser“
}
}
]
}
}
TASK [create-windows-share : Give full control on share folder] **********************************************************************************************************************
changed: [‘devops.nicktailor.win] => (item={‘share_name‘: ‘test3’, ‘description_share‘: ‘default share for testing’, ‘share_path‘: ‘C:\\inetpub\\wwwroot3′, ‘change’: ‘ansibleuser‘, ‘list’: True, ‘allowed_users‘: ‘ansibleuser‘, ‘user_permissions‘: ‘ansibleuser‘})
TASK [create-windows-share : debug] **************************************************************************************************************************************************
ok: [‘devops.nicktailor.win] => {
“permission”: {
“changed”: true,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: true,
“failed”: false,
“item”: {
“allowed_users“: “ansibleuser“,
“change”: “ansibleuser“,
“description_share“: “default share for testing”,
“list”: true,
“share_name“: “test3”,
“share_path“: “C:\\inetpub\\wwwroot3″,
“user_permissions“: “ansibleuser“
}
}
]
}
}
PLAY RECAP ***************************************************************************************************************************************************************************
‘devops.nicktailor.win : ok=7 changed=3 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
How to deploy multiple sites in IIS with Ansible
This was fun and interesting little project. Looks like nobody ever really got it working properly, so I decided to do it.
You can also upload your own custom web.config
- Ability to create multiple application pools per site.
- Set application pool identities
- Update IIS site paths to use a NAS location vs physical paths only
Note: You will likely have to add the firewall rules depending on how your network setup. I have written a windows playbook to handle the firewall stuff, but that will be in another post. You will also need to ensure winrm is configured properly on the windows machine for ansible to talk to it.
Ansible Operational Documentation:
Example file: hosts.dev, hosts.staging, hosts.prod
Note: If there is no group simply list the server outside grouping, the –limit flag will pick it
up.
Descriptions:
Operational Use:
Descriptions:
Operational Use:
Okay now here is where VSC is handy. You want to connect your visual studio code to the management server under your user.
Note: You don’t have to use VSC you can use good old nano or vim, but it’s a pain. Up to you.
Example files:
ansible/inventory/dev/host_vars/devops.nicktailor.win
Example Yaml Block :
domains:
– name: “First website”
host_header: ”
ip: ‘*’
iis_binding_port: ‘8082’
protocol: ‘http’
state: ‘absent’
certificate_hash: ”
certificate_store_name: ‘My’
iis_site_name: ‘Default Web Site’
iis_site_path: ‘C:\inetpub\wwwroot1′
iis_acl_path: ‘C:\inetpub\wwwroot1′
iis_site_state: absent
iis_site_port: ’80’
iis_site_id: ”
iis_site_ip: ‘*’
iis_site_ssl: false
iis_site_hostname: ‘*’
iis_site_parameters: ”
iis_site_state_start: stopped
iis_site_web_config: ”
iis_site_web_config_force: true
– name: “Second website”
host_header: ”
ip: ‘*’
iis_binding_port: ‘8081’
protocol: ‘http’
state: ‘present’
certificate_hash: ”
certificate_store_name: ‘My’
iis_site_name: ‘site2’
iis_acl_path: ‘C:\inetpub\wwwroot2′
iis_site_path: ‘C:\inetpub\wwwroot2′
iis_site_state: present
iis_site_port: ’80’
iis_site_id: ”
iis_site_ip: ‘*’
iis_site_ssl: false
iis_site_hostname: ‘*’
iis_site_parameters: ”
iis_site_state_start: started
iis_site_web_config: ”
iis_site_web_config_force: true
Running your playbook:
Example: of ansible/nickwiniis.yml
– hosts: all
gather_facts: yes
any_errors_fatal: true
roles:
– role: ansible-role-win-iis
Command:
ansible-playbook –i inventory/dev/hosts nickwiniis.yml -u nick –Kkb –limit=’devops.nicktailor.win‘
Successful example run of the book:
[ntailor@ansible.nicktailor.com]$ ansible–playbook –i hosts/dev nickwiniis.yml —limit=‘devops.nicktailor.win‘
PLAY [all] *****************************************************************************************************************************************************
TASK [Gathering Facts] *****************************************************************************************************************************************
ok: [devops.nicktailor.win]
TASK [ansible–role–win–iis : ensure iis is installed] **********************************************************************************************************
ok: [devops.nicktailor.win]
TASK [ansible–role–win–iis : configure app pool] ***************************************************************************************************************
ok: [devops.nicktailor.win]
TASK [ansible–role–win–iis : ensure path for site exists] ******************************************************************************************************
ok: [devops.nicktailor.win] => (item={‘name’: ‘First website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8082’, ‘protocol’: ‘http’, ‘state’: ‘absent’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘Default Web Site’, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_site_state‘: ‘absent’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘stopped’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
ok: [devops.nicktailor.win] => (item={‘name’: ‘Second website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8081’, ‘protocol’: ‘http’, ‘state’: ‘present’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘site2’, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_state‘: ‘present’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘started’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
TASK [ansible–role–win–iis : debug] ****************************************************************************************************************************
ok: [devops.nicktailor.win] => {
“path”: {
“changed”: false,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: false,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot1″,
“iis_binding_port“: “8082”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “Default Web Site”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot1″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “absent”,
“iis_site_state_start“: “stopped”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “First website”,
“protocol”: “http”,
“state”: “absent”
}
},
{
“ansible_loop_var“: “item”,
“changed”: false,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot2″,
“iis_binding_port“: “8081”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “site2”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot2″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “present”,
“iis_site_state_start“: “started”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “Second website”,
“protocol”: “http”,
“state”: “present”
}
}
]
}
}
TASK [ansible–role–win–iis : allow iis group access to site path] **********************************************************************************************
ok: [devops.nicktailor.win] => (item={‘name’: ‘First website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8082’, ‘protocol’: ‘http’, ‘state’: ‘absent’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘Default Web Site’, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_site_state‘: ‘absent’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘stopped’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
ok: [devops.nicktailor.win] => (item={‘name’: ‘Second website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8081’, ‘protocol’: ‘http’, ‘state’: ‘present’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘site2’, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_state‘: ‘present’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘started’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
TASK [ansible–role–win–iis : debug] ****************************************************************************************************************************
ok: [devops.nicktailor.win] => {
“access”: {
“changed”: false,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: false,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot1″,
“iis_binding_port“: “8082”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “Default Web Site”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot1″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “absent”,
“iis_site_state_start“: “stopped”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “First website”,
“protocol”: “http”,
“state”: “absent”
}
},
{
“ansible_loop_var“: “item”,
“changed”: false,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot2″,
“iis_binding_port“: “8081”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “site2”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot2″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “present”,
“iis_site_state_start“: “started”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “Second website”,
“protocol”: “http”,
“state”: “present”
}
}
]
}
}
TASK [ansible–role–win–iis : upload custom web.config from template] *******************************************************************************************
skipping: [devops.nicktailor.win] => (item={‘name’: ‘First website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8082’, ‘protocol’: ‘http’, ‘state’: ‘absent’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘Default Web Site’, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_site_state‘: ‘absent’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘stopped’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
skipping: [devops.nicktailor.win] => (item={‘name’: ‘Second website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8081’, ‘protocol’: ‘http’, ‘state’: ‘present’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘site2’, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_state‘: ‘present’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘started’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
TASK [ansible–role–win–iis : debug] ****************************************************************************************************************************
ok: [devops.nicktailor.win] => {
“startiis“: {
“changed”: false,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot1″,
“iis_binding_port“: “8082”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “Default Web Site”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot1″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “absent”,
“iis_site_state_start“: “stopped”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “First website”,
“protocol”: “http”,
“state”: “absent”
},
“skip_reason“: “Conditional result was False”,
“skipped”: true
},
{
“ansible_loop_var“: “item”,
“changed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot2″,
“iis_binding_port“: “8081”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “site2”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot2″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “present”,
“iis_site_state_start“: “started”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “Second website”,
“protocol”: “http”,
“state”: “present”
},
“skip_reason“: “Conditional result was False”,
“skipped”: true
}
]
}
}
TASK [ansible–role–win–iis : configure site] *******************************************************************************************************************
changed: [devops.nicktailor.win] => (item={‘name’: ‘First website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8082’, ‘protocol’: ‘http’, ‘state’: ‘absent’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘Default Web Site’, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_site_state‘: ‘absent’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘stopped’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
changed: [devops.nicktailor.win] => (item={‘name’: ‘Second website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8081’, ‘protocol’: ‘http’, ‘state’: ‘present’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘site2’, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_state‘: ‘present’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘started’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
TASK [ansible–role–win–iis : debug] ****************************************************************************************************************************
ok: [devops.nicktailor.win] => {
“iis_site“: {
“changed”: true,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: true,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot1″,
“iis_binding_port“: “8082”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “Default Web Site”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot1″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “absent”,
“iis_site_state_start“: “stopped”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “First website”,
“protocol”: “http”,
“state”: “absent”
},
“site”: {
“ApplicationPool“: “DefaultAppPool“,
“Bindings”: [
“*:80:*“
],
“ID”: 1,
“Name”: “Default Web Site”,
“PhysicalPath“: “C:\\inetpub\\wwwroot1″,
“State”: “Stopped”
}
},
{
“ansible_loop_var“: “item”,
“changed”: true,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot2″,
“iis_binding_port“: “8081”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “site2”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot2″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “present”,
“iis_site_state_start“: “started”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “Second website”,
“protocol”: “http”,
“state”: “present”
},
“site”: {
“ApplicationPool“: “DefaultAppPool“,
“Bindings”: [
“*:80:*“
],
“ID”: 2,
“Name”: “site2”,
“PhysicalPath“: “C:\\inetpub\\wwwroot2″,
“State”: “Started”
}
}
]
}
}
TASK [ansible–role–win–iis : configure site bindings] **********************************************************************************************************
ok: [devops.nicktailor.win] => (item={‘name’: ‘First website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8082’, ‘protocol’: ‘http’, ‘state’: ‘absent’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘Default Web Site’, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot1′, ‘iis_site_state‘: ‘absent’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘stopped’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
changed: [devops.nicktailor.win] => (item={‘name’: ‘Second website’, ‘host_header‘: ”, ‘ip‘: ‘*’, ‘iis_binding_port‘: ‘8081’, ‘protocol’: ‘http’, ‘state’: ‘present’, ‘certificate_hash‘: ”, ‘certificate_store_name‘: ‘My’, ‘iis_site_name‘: ‘site2’, ‘iis_acl_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_path‘: ‘C:\\inetpub\\wwwroot2′, ‘iis_site_state‘: ‘present’, ‘iis_site_port‘: ’80’, ‘iis_site_id‘: ”, ‘iis_site_ip‘: ‘*’, ‘iis_site_ssl‘: False, ‘iis_site_hostname‘: ‘*’, ‘iis_site_parameters‘: ”, ‘iis_site_state_start‘: ‘started’, ‘iis_site_web_config‘: ”, ‘iis_site_web_config_force‘: True})
TASK [ansible–role–win–iis : debug] ****************************************************************************************************************************
ok: [devops.nicktailor.win] => {
“startiis2”: {
“changed”: true,
“msg“: “All items completed”,
“results”: [
{
“ansible_loop_var“: “item”,
“changed”: false,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot1″,
“iis_binding_port“: “8082”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “Default Web Site”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot1″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “absent”,
“iis_site_state_start“: “stopped”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “First website”,
“protocol”: “http”,
“state”: “absent”
}
},
{
“ansible_loop_var“: “item”,
“binding_info“: {
“bindingInformation“: “*:8081:”,
“certificateHash“: “”,
“certificateStoreName“: “”,
“hostheader“: “”,
“ip“: “*”,
“port”: 8081,
“protocol”: “http”,
“sslFlags“: 0
},
“changed”: true,
“failed”: false,
“item”: {
“certificate_hash“: “”,
“certificate_store_name“: “My”,
“host_header“: “”,
“iis_acl_path“: “C:\\inetpub\\wwwroot2″,
“iis_binding_port“: “8081”,
“iis_site_hostname“: “*”,
“iis_site_id“: “”,
“iis_site_ip“: “*”,
“iis_site_name“: “site2”,
“iis_site_parameters“: “”,
“iis_site_path“: “C:\\inetpub\\wwwroot2″,
“iis_site_port“: “80”,
“iis_site_ssl“: false,
“iis_site_state“: “present”,
“iis_site_state_start“: “started”,
“iis_site_web_config“: “”,
“iis_site_web_config_force“: true,
“ip“: “*”,
“name”: “Second website”,
“protocol”: “http”,
“state”: “present”
},
“operation_type“: “added”,
“website_state“: “Started”
}
]
}
}
RUNNING HANDLER [ansible–role–win–iis : restart iis] ***********************************************************************************************************
changed: [devops.nicktailor.win]
PLAY RECAP *****************************************************************************************************************************************************
devops.nicktailor.win : ok=13 changed=3 unreachable=0 failed=0 skipped=1 rescued=0 ignored=0
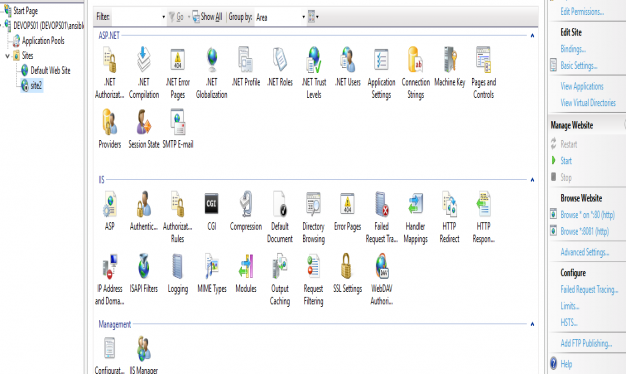
Now you could write in to copy an test index.html file, but just to show it works. I manually created the index.html
Test:
[ansible.nicktailor.com]$ curl -k http://devops.nicktailor.win
YAY THis works!
